
What is Log Management? Definition, Best Practices, and Benefits
What is log management, and what are the best practices and challenges of managing your application and server logs? This article will take you through the ins and outs of log management, giving you effective strategies to collect logs for high performance and security.
Key Takeaways
- Insight into log management and its significance in maintaining system performance and data security.
- Understand the log management process, including log collection, aggregation, parsing, normalization, correlation of events, and analysis.
- Benefits of log management such as data security, compliance, operational insight, and centralized data management.
- Detailed overview of challenges, including high log data volume, log collection complexity, and log security.
- A look at the role of the CloudPanel Log Viewer for effective logging.
- Answers to FAQs, providing a comprehensive understanding of log management.
- Best practices in log management and its positive impact on businesses.
Definition and Importance of Log Management
Log management collects, aggregates, parses, normalizes, and analyzes log data from various sources. It helps gain meaningful insights into the performance and security of applications and infrastructure.
Effective log management is crucial for identifying issues, troubleshooting problems, detecting security threats, and ensuring compliance. It involves using log management software or tools to centralize log data. The data is in a standardized format for easy monitoring and analysis.
What is Log Management?
Log management is a critical aspect of many IT systems that involves tracking, storing, and analyzing computer-generated logs. As networks grow in complexity, managing system logs becomes more challenging.
Yet it's essential to maintain the health and security of an organization’s data infrastructure. It involves collecting log data from various sources, including operating systems, applications, and devices. This collected information is then analyzed to identify any performance issues or security threats within the system.
The log management process also includes aggregation, where all the logs are pooled together for easier analysis. The next phase is parsing, separating each element in your logs into organized structures.
The last stage, normalization, transforms diverse log formats into a standard form for easy comparison. It offers quick correlation for efficient monitoring and response times to possible incidents.
What is the Importance of Logging?
Logging serves two essential purposes: troubleshooting and security. Recording all system activities in log files is crucial for easy tracking of potential issues. In case of any performance decline or discrepancy, logs provide a trail to identify the root cause effectively.
For maintaining robust security, logs are invaluable as they record all user actions. It helps spot suspicious behavior promptly.
Benefits of log management and monitoring
Effective log management and monitoring are crucial in maintaining the overall health of systems and applications. Here are some key benefits:
-
Enhancing Data Security: Log management tools can identify security threats or breaches, helping maintain data security.
-
Troubleshooting: Log files give insights into system performance and application issues, making troubleshooting quicker and more efficient.
-
Compliance: For industries like healthcare, robust log management is necessary to comply with regulations. It includes PCI DSS, Health Insurance Portability and Accountability Act.
-
Audit Trails: Logs collect data that is part of audit trails required for forensics or regulatory purposes.
-
Optimizing System Performance: Regular log monitoring can catch performance issues early, preventing downtime and optimizing system operations.
-
Gaining Operational Insight: Log data analysis can provide valuable operational insights to improve processes and make informed decisions.
-
Centralizing Data Management: Centralized log aggregation helps organize data from multiple sources at a centralized location for easier management.
-
Unstructured Data: Tools such as log parsers help transform unstructured logs into meaningful insights enhancing the analysis process.
Log Management Processes and Best Practices
We’ll look at the steps in the log management processes and best practices. It includes log collection, aggregation, parsing, normalization, event log correlation, and analysis.
1. Log collection
Log collection is an essential step in effective log management. The process involves gathering log data from various sources, such as your infrastructure. You gain valuable insights into system performance and security events.
Organizations can monitor response times, detect performance issues, and identify potential security threats by collecting logs. With the ability to collect and analyze logs effectively, businesses can enhance their operational performance and proactively address any issues.Additionally, including contact information on business cards can be a helpful way to encourage networking and collaboration.
2. Log aggregation
Log aggregation involves collecting logs from various sources. It includes applications, servers, and network devices, in a centralized location.
By aggregating logs, you can view their system's health and performance overall. It allows for easier troubleshooting of issues, identifying security threats, and detecting anomalous activities.
With the help of log aggregation tools or software, companies can efficiently collect and organize terabytes of log data in real-time or near-real-time for analysis and visualization purposes.
3. Log parsing
Log parsing involves analyzing and extracting valuable information from log files. By parsing logs, you can effectively identify patterns, detect errors or security threats, and gain meaningful insights into system performance.
Log parsing helps organize unstructured data into a standardized format for easier analysis and visualization. With the help of log parsing tools or software, security teams can quickly search vast amounts of log data to identify security incidents. It plays a crucial role in maintaining the health and security of IT systems.
4. Log normalization
Log normalization is a crucial step in effective log management. It involves transforming raw log data into a standardized format, making analyzing and comparing logs easier.
By normalizing logs, organizations can gain meaningful insights from their data. Log normalization ensures that logs from various sources are organized, enabling efficient analysis.
5. Correlation of events
When managing logs, one important aspect is the correlation of events. It involves analyzing log data to identify patterns and relationships between different events.
Effective correlation helps in understanding the cause-and-effect relationship between various events. It enables you to make informed decisions and improve overall operational efficiency. The correlation of events also enhances visibility and allows prompt response to issues.
6. Log analysis
Log analysis examines log data to gain valuable insights into their systems. You can then take proactive measures to address any issues. Users can search, filter, and visualize log data using log analysis tools and techniques to better learn about their systems.
Challenges in Log Management System
1. Different log formats
Managing logs can become challenging when dealing with logs generated in different formats. It makes it difficult to analyze and extract meaningful insights.
2. A high volume of log data
Managing a large volume of log data requires efficient storage and processing capabilities. That’s the way to ensure quick retrieval and analysis.
3. Log collection complexity
Collecting logs from various sources, such as applications, operating systems, and infrastructure, can be complex. You’ll require careful configuration with logging tools.
4. Log security
Protecting sensitive log data from unauthorized access or tampering is crucial for maintaining data security and compliance.
5. Scalability issues
As systems grow in size and complexity, logs need to scale effectively. It should easily handle the increasing amount of log data without compromising performance.
6. Log correlation challenges
Correlating events across multiple logs can be challenging, especially when dealing with diverse systems that generate different types of logs.
7. Real-time monitoring
Monitoring real-time logs is essential for detecting events requiring immediate attention. However, ensuring efficient real-time log monitoring can be a complex task. You can find logging tools that allow you to gain near real-time logging data.
8. Data overload
Analyzing massive amounts of log data can be overwhelming if proper techniques are not used to filter out irrelevant information and focus on important data.
9. Unstructured log data
Logs sometimes contain unstructured data that needs a standard format. It is important to filter the data to parse and analyze without additional processing steps.
10. Log retention policies
It is determining the right time frame for retaining logs. Considering compliance requirements and storage capacity can pose challenges in effective log management.
Scalable services
Scalable services are an essential aspect of effective log management. With the increasing volume of log data generated, it is crucial to have scalable services in place.
Scalable services ensure that log collection, aggregation, parsing, normalization, correlation of events, and analysis processes can efficiently process large amounts of data. It should not compromise performance or response times. With scalable services in your log management system, you can easily scale up as your log data grows.
Log security
Log security protects log data from unauthorized access, tampering, or theft. Using robust security measures, you can ensure the integrity and confidentiality of their logs. It includes employing encryption techniques to safeguard sensitive log information and restricting access rights to authorized personnel only.
Logging systems should be regularly monitored for any suspicious activity. Such proactive measures help maintain the privacy and reliability of log data. It allows you to identify and respond to security incidents on time effectively.
CloudPanel Log Viewer
The CloudPanel Log Viewer is a helpful feature that allows users to gain valuable insights by directly offering access to NGINX and PHP-FPM log files.
Every activity performed is captured in these logs. It provides diagnostic information, monitors user activities, troubleshoots software errors, and detects security breaches.
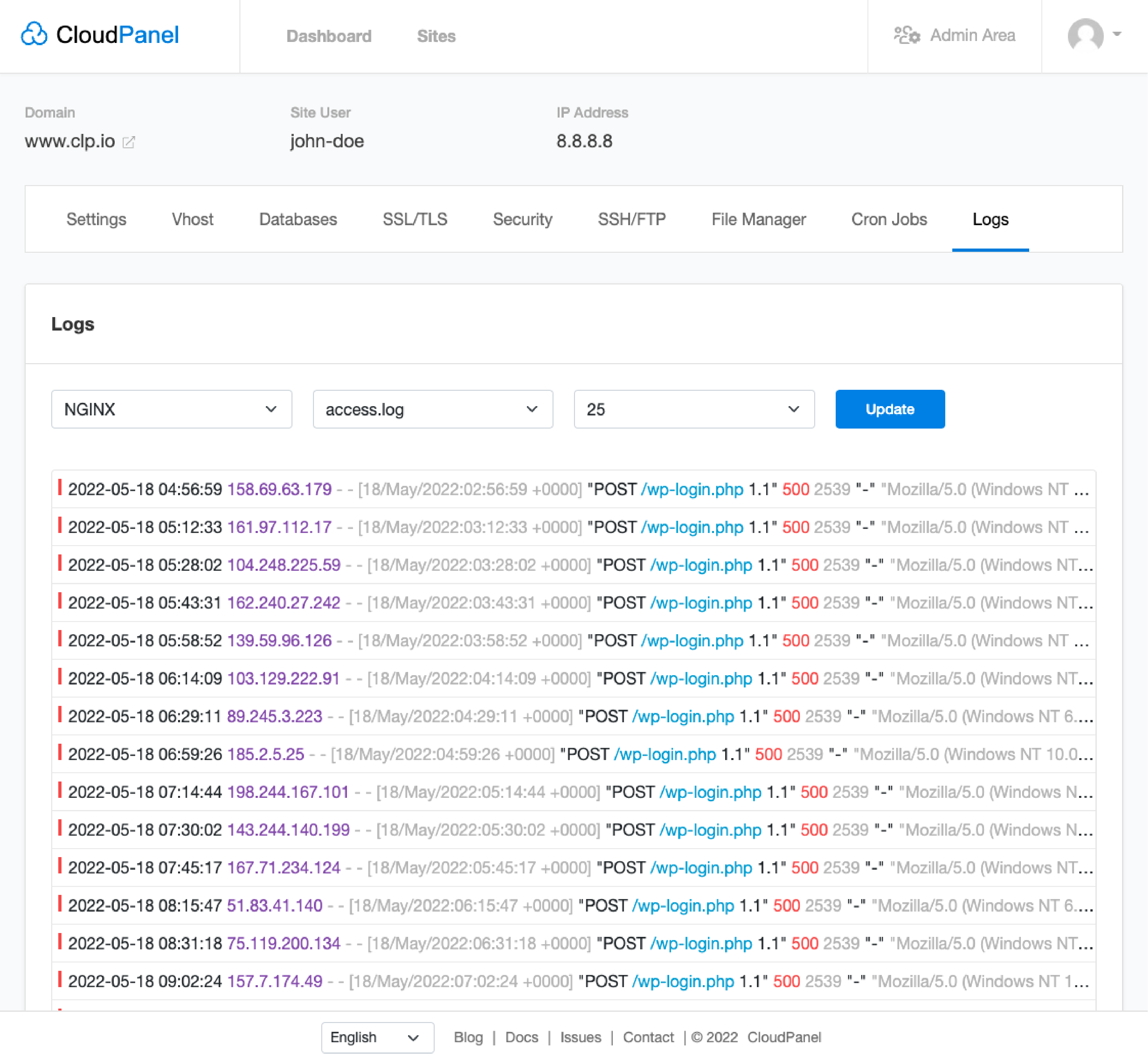
1. NGINX Log Files
NGINX is a powerful web server software. Its log files contain valuable information about the operational status, transactions made, client requests, server responses, and errors, among other details. The data helps you understand user behavior patterns, monitor server performance, and troubleshoot issues swiftly.
For example, if a client’s request led to a server error, you could pinpoint and resolve the issue using the data from the NGINX log files.
2. PHP-FPM Log Files
PHP-FPM (FastCGI Process Manager) is an alternative PHP FastCGI with additional features useful for high-demand websites. It's widely used for improving PHP application performance and controlling resource usage.
Its log files provide detailed error messages useful for identifying issues in your PHP scripts. It tracks PHP errors, warnings, parse errors, and notices. You can diagnose problems that affect your website's performance and usability.
For example, if a PHP script generates an error, it would be logged in the PHP-FPM log files. It helps enable faster debugging and resolution.
FAQs
1. What is an effective log management system?
An effective log management system is a solution that helps organizations collect log data from various sources, analyze it, and store it efficiently. This aids in diagnosing issues, spotting security threats, and ensuring regulatory compliance.
2. Why is log collection important?
Log collection is crucial as it provides valuable data that can be used to pinpoint the root cause of any issues in your IT environment. Regular log collection can help prevent future problems and identify areas for improvement.
3. How do log management tools help with regulatory compliance?
Log management tools maintain a recorded trail of all activities. This assists in maintaining regulatory compliance by providing easy access to information required for audits.
4. How does an effective log management solution combat security threats?
An effective log management solution can detect strange patterns or anomalies promptly, signaling potential security threats. It allows for quick action to be taken to prevent any security breaches.
5. Why are real-time insights essential in log management?
Real-time insights from logs enable an immediate response to any issue that arises. This aids in maintaining the system's optimal performance and upgrading security measures, making well-rounded log management solutions essential.
6. What role does an event log play in an effective log management system?
An event log systematically records any significant incidents within a system. This integral component of an effective log management system offers a chronological account of operations, enabling you to trace the root cause of any issues.
7. Why is centralized log management important for businesses?
Centralized log management is crucial for businesses as it provides a centralized and comprehensive solution for monitoring and analyzing log files from various sources.
With a robust centralized log management solution, businesses can easily manage and secure their log files. You gain important insights into system performance and potential security threats.
Using centralized log management systems, organizations can optimize their log management processes, ensuring data integrity, regulatory compliance, and enhanced operational efficiency.
Summary
This article covers what log management is, its importance, its benefits, and associated challenges. It also explores key processes like log collection, aggregation, parsing, normalization, correlation of events, and analysis.
We explore the CloudPanel Log Viewer, which helps access NGINX and PHP-FPM log files for easy log management. To start analyzing your logs, check out the free CloudPanel.




