
What are SSH Keys and How to Use Them?
What are SSH keys? SSH (Secure Shell) keys are access credentials used in the SSH protocol. These are foundational to modern cloud infrastructures like AWS, Google Cloud, and Azure. This article explores the definition and purpose of SSH keys, highlighting their advantages over traditional passwords. We cover insights on generating, storing, and managing them securely. Gain a better understanding of SSH keys and enhance your server access security.
Key Takeaways
- Discover what SSH keys are and how they enhance server access security.
- Learn about encryption, with public and private keys working like locks and keys to establish secure connections.
- Explore the advantages of SSH key authentication, including stronger security, easier access management, and asymmetric encryption.
- Gain practical insights into effectively generating, storing, and managing SSH keys.
- Implement best practices such as regular key updates, access restriction, monitoring, and auditing to maintain a robust security posture.
- Learn about Cloud IAM for centralized control and simplifying SSH key management in cloud environments.
- Enhance server access security by utilizing SSH key agents for additional protection and convenience.
- Discover how to manage SSH users with CloudPanel, enabling easy user addition, deletion, and password changes.
SSH Keys Definition and Overview
The Secure Shell keys are encrypted files that authenticate and establish secure communication between clients and servers. It provides faster access than traditional password-based authentication.
These keys are generated in pairs:
- A public key that is shared with the server.
- A corresponding private key is kept securely on the client's machine.
SSH keys are a way to prove who you are when using a computer. They come in pairs and work like locks and keys. The public key is the lock, and the private key is the key that fits it. You put your public key on any system you want to enter. When you connect, the system checks if your private key matches the public one saved there. If the key matches, then you can get in. It's safer than passwords because keys are hard to guess or steal. It provides secure access between two systems.
How does SSH key authentication work?
SSH key authentication is a way to prove your identity when logging into a server using a pair of keys. The public key is placed on the server, while the user keeps the private key securely.
When attempting to log in, the server uses the public key to issue a challenge. The user's computer uses the private key to respond to the challenge. If the response matches what the server expects, access is granted.
Access is denied if there is no match, ensuring security from unauthorized individuals. The SSH key pair is used to authenticate the user's or process's identity, encrypt messages, and establish a secure connection between the client and server. The challenge-response sequence happens automatically, without any manual intervention from the user.
Advantages of SSH key authentication over passwords
SSH key authentication offers several benefits over traditional password-based authentication.
1. Higher Security Level
SSH keys provide a higher level of security compared to passwords. Since the keys are longer and more complex than typical passwords, they are less susceptible to brute force attacks or password guessing.
2. Access Management
The Secure Shell keys eliminate the need for users to remember and manage multiple passwords for different systems. With SSH key authentication, users only need their private key. It makes it easier and more convenient to access remote servers.
3. Asymmetric Encryption
SSH key pairs are asymmetrically encrypted. If someone gains unauthorized access to the public key on a server, they still cannot derive the corresponding private key needed for authentication.
How to Use SSH Keys?
The section covers how to generate, store, and manage the keys on different operating systems, ensuring secure access to remote servers.
Generating SSH keys on Linux/Mac and Windows
To generate the Secure Shell keys on Linux/Mac and Windows:
- Open a command line interface.
- For Linux/Mac, use the
ssh-keygencommand to generate the keys.
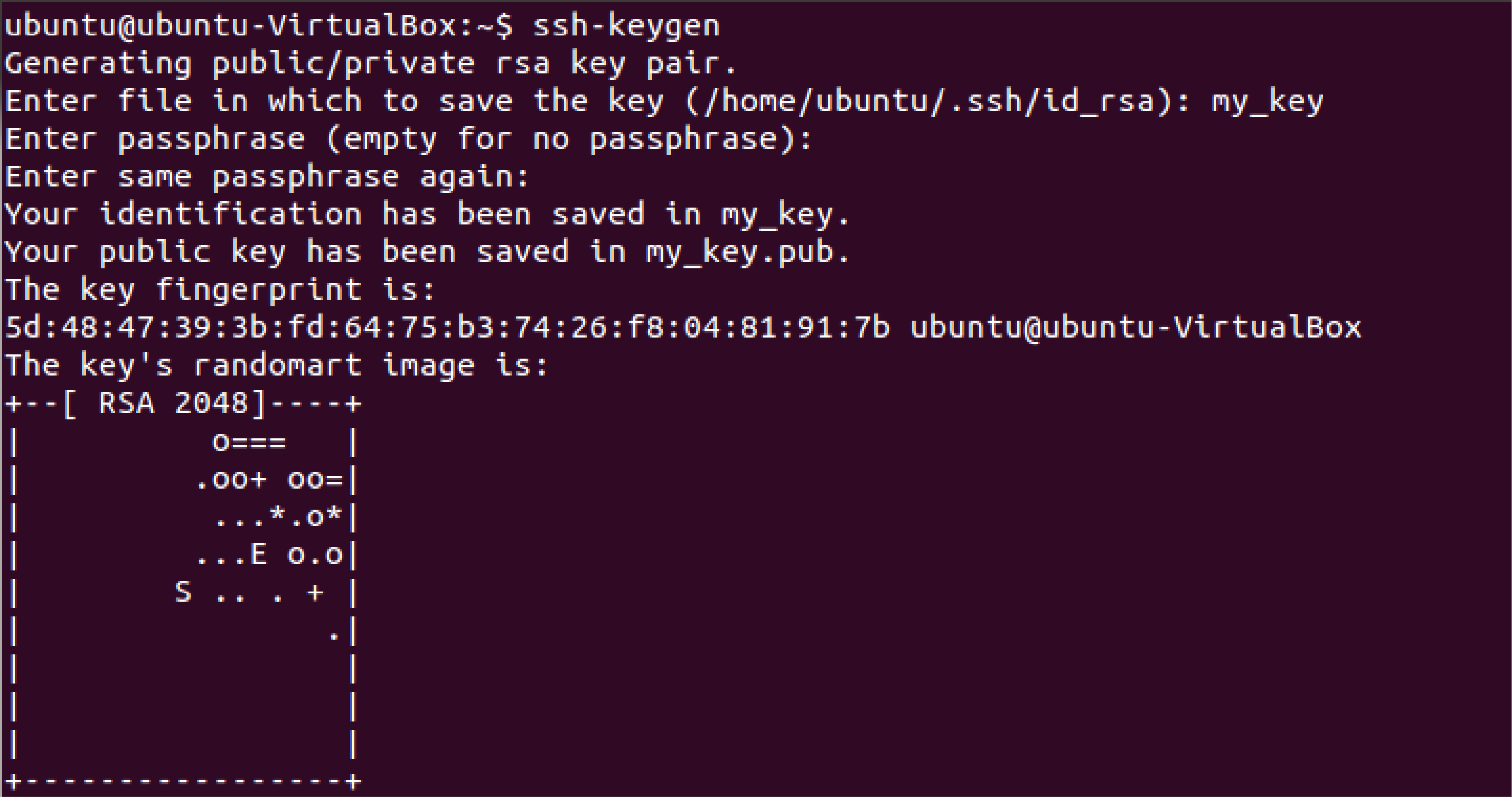
- Specify the type of encryption key - usually RSA or Ed25519.
- Choose a secure passphrase for your private key (optional but recommended).
- Save the generated keys in a specific directory by specifying the file path.
- For Windows, download and install an SSH client like PuTTY or Git Bash.
- Open the client and use the
ssh-keygencommand to generate the keys, following similar steps as on Linux/Mac. - Once generated, you will have a public key (
id_rsa.pub) and a private key (id_rsa) pair.
Storing SSH keys securely
To ensure the security of SSH keys, it's important to store them correctly. One way to do this is using a secure storage location, such as a dedicated SSH key directory on your computer or server.
The directory should have proper access controls to restrict who can read, write, and execute its files. It's also recommended to encrypt the SSH private key with a passphrase for an extra layer of protection.
Consider using a hardware token or smart card to store your SSH key securely offline. These methods will help prevent unauthorized access and protect your keys from being compromised.
Cloud IAM for SSH key management
Cloud IAM (Identity and Access Management) is an important aspect of SSH key management. With Cloud IAM, you can centrally manage and control access to your keys across different cloud services and platforms.
It provides a secure and efficient way to grant or revoke access to SSH keys. Only authorized individuals can gain access to your remote servers. Using IAM for SSH key management, you can easily generate, store, rotate, and monitor your SSH keys. It helps maintain a strong security posture and streamline operations.
Best Practices for SSH Key Usage
1. Regularly updating and rotating SSH keys
-
Update your keys periodically to protect against unauthorized access.
-
Rotate your keys regularly to prevent security breaches.
-
Keep track of when you last updated or rotated your SSH keys.
-
Set a schedule or reminder to ensure regular updates and rotations of your SSH keys.
-
Consider an automated process for updating and rotating SSH keys.
-
Check for any vulnerabilities in your current SSH key setup.
-
Stay informed about the latest best practices for updating and rotating SSH keys.
-
Consult with security experts to ensure you follow the recommended guidelines.
2. Limiting access and permissions for SSH keys
-
Grant access only to authorized users: Only give SSH key access to individuals who require it for their roles or responsibilities.
-
Use a naming convention for SSH keys: Assign unique and descriptive names to each SSH key to identify the purpose and associated user easily.
-
Restrict access based on IP addresses: Configure firewall rules to allow SSH key access only from specific IP addresses or ranges.
-
Enforce strong passphrase policies: Encourage users to use strong passphrases for their private keys and regularly update them.
-
Implement role-based access control (RBAC): Utilize RBAC mechanisms provided by your operating system or cloud platform to define granular permissions for SSH key usage.
-
Regularly review and revoke unnecessary keys: Periodically audit your Secure Shell keys and remove any that are no longer needed or are associated with inactive users.
-
Monitor SSH key activity: Set up logging and monitoring systems to track SSH key usage. Detect any suspicious activities, and respond promptly if any anomalies are detected.
-
Educate users about secure practices: Train your users on best practices for handling and protecting their SSH keys. It includes not sharing them with others or storing them insecurely.
-
Implement multi-factor authentication (MFA): Consider using MFA in addition to SSH key authentication for an extra layer of security.
Monitoring and auditing SSH key usage
-
Keep track of all SSH key activity, including when keys are generated, used, and revoked.
-
Monitor for any unauthorized use or access attempts using SSH keys.
-
Implement logging and auditing mechanisms to capture relevant information about SSH key usage.
-
Regularly review logs and audit trails to identify any suspicious or anomalous activity related to SSH key usage.
-
Use monitoring tools or software to provide real-time alerts and notifications for potential security issues with SSH keys.
-
Establish clear policies and procedures for monitoring and auditing SSH key usage. It includes regularly reviewing access controls and permissions associated with each key.
-
Conduct periodic reviews and audits of SSH key management practices. It ensures compliance with best practices and industry standards.
Using SSH key agents for added security
SSH key agents provide an added layer of security when using SSH keys. These agents act as secure storage for your private keys and allow you to authenticate with remote servers without re-entering your passphrase each time.
Using an SSH key agent can avoid the risk of someone intercepting or stealing your private key. An SSH agent stores your private key in memory while you're logged into your computer. It eliminates the need to keep the private key on disk, which could be vulnerable to theft or unauthorized access.
To use an SSH agent, you simply add your private key to the agent and start it up. Once the agent runs, any SSH connections that require authentication will automatically use the stored private key from the agent's memory.
How to Add SSH Users with CloudPanel?
You can add SSH users on CloudPanel directly with the following steps:
Add an SSH User
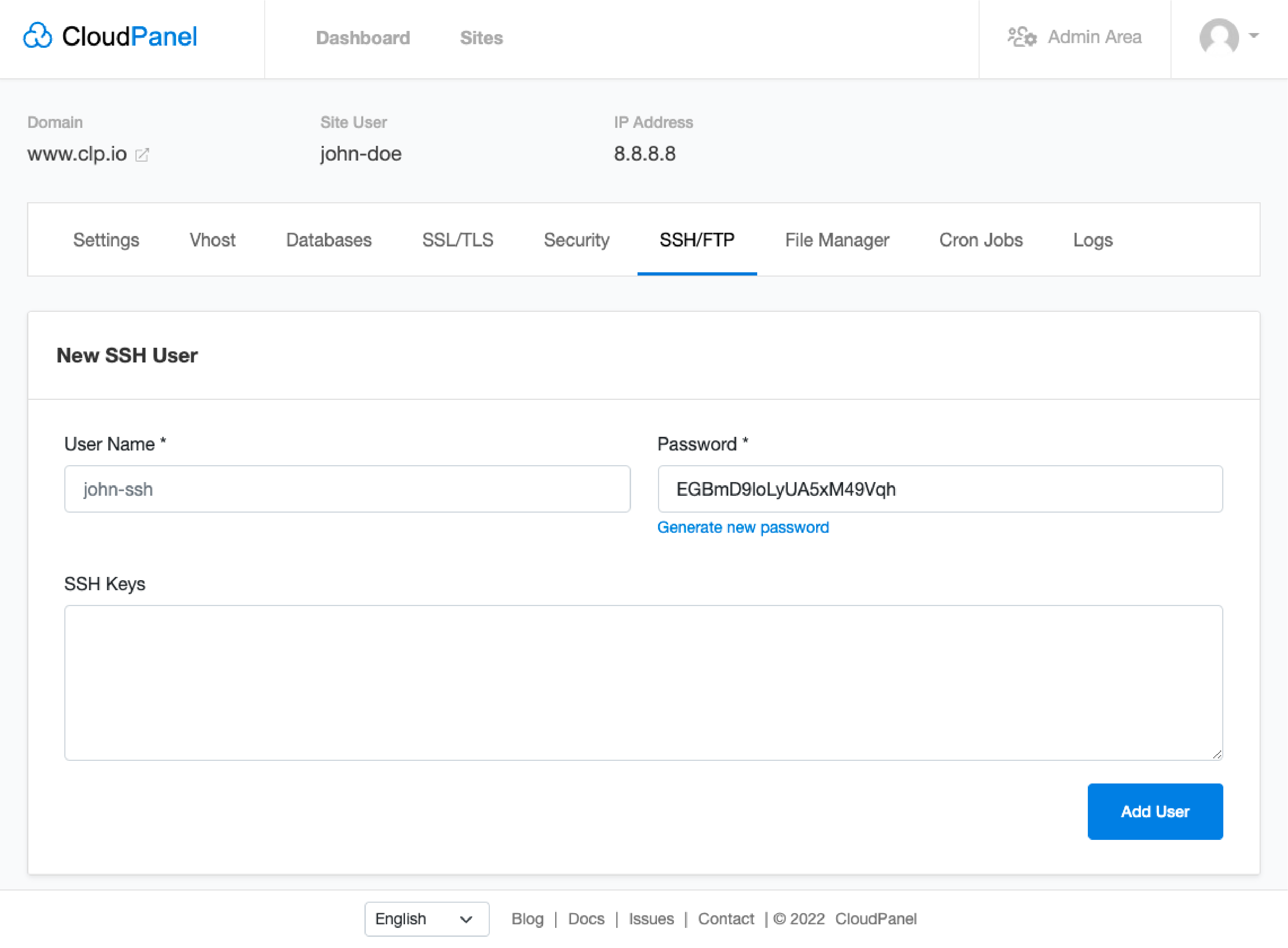
- Go to the SSH/FTP tab in your CloudPanel.
- Fill in the form with the username and password of the new user.
- Add your Public SSH keys if you want to log in via Public Key authentication.
- Click the Add User button.
FAQs:
1. What is the SSH key used for?
SSH key is used for the SSH protocol, commonly identified as a session key. It enhances security during remote logins by generating encrypted data and providing secure and unbreachable connections.
2. How do I generate SSH keys?
You can use the command-line interface on your computer to generate SSH keys. You can also use various software tools that provide an interface for creating and managing SSH keys.
3. How do I use The Secure Shell keys to connect to remote servers?
To use the keys for connecting to remote servers, you need to add your public key to the server's authorized_keys file. It allows secure authentication without requiring a password each time you connect.
4. Are SSH keys more secure than passwords?
Yes, using the keys is generally more secure than passwords because they provide stronger encryption and cannot easily be guessed or brute-forced by attackers like passwords often can.
5. What is an example of an SSH key?
An example of an SSH key can be ssh-id-rsa This is an RSA key often stored in an SSH authorized_keys file. It is especially important for maintaining secure connections in Windows systems.
6. Where do I find my SSH key?
You can find your SSH key typically in your user profile's file named '.ssh'. The keys are stored in a file specified by the user on Windows systems. It typically prompts you for "a file to save the key" during SSH key generation.
7. What is an SSH or RSA key?
SSH or RSA key represents a method of secure shell encryption. It aids in the creation of a secure connection between the client and the server, reducing the risk of unauthorized access. SSH (Secure Shell) is a protocol, while RSA is a type of SSH key used to add an extra layer of security.
8. How does configuration management tools use SSH keys to secure access to remote servers?
Configuration management tools utilize SSH key authentication to provide a secure mechanism to access remote servers. It involves a pair of private and public keys, commonly called SSH keys.
The public key is shared with the remote server, and the private key remains securely with the user. When the user attempts to connect, the server issues a challenge, encrypted with the public key stored on the server. The user's computer uses the private key to respond.
If the response matches, access to the server is granted. This encryption key-based method is safer against brute force attacks compared to traditional passwords. Therefore, ensuring controlled SSH authentication also makes it easier to manage SSH keys across the network. It is useful when leveraging professional SSH key management software.
9. Can the SSH protocol assist in addressing potential vulnerabilities in SSH key management?
Yes, the SSH protocol plays a crucial role in maintaining secure SSH key management. It requires both private and public keys for successful authentication, ensuring that even if a public key on a remote server gets compromised. The intruder would not be granted access as the private key remains confidential.
It minimizes the risk of unauthorized access, even in the face of brute force attacks. Using an SSH key management tool can simplify the process of managing SSH keys across various users and servers. It provides automated scheduling for updates and revocation of old or unnecessary keys. This boosts server security and offers robust SSH authentication.
Summary
The article covered what SSH keys are. It’s important for secure server access. It provides a more secure and convenient alternative to passwords by using public-key cryptography. We discussed their advantages, such as stronger security and easier access management. You gained practical steps on generating, storing, and managing SSH keys. With CloudPanel, you can directly manage SSH/FTP users for secure and easy user management.



